Play Lucky Jet
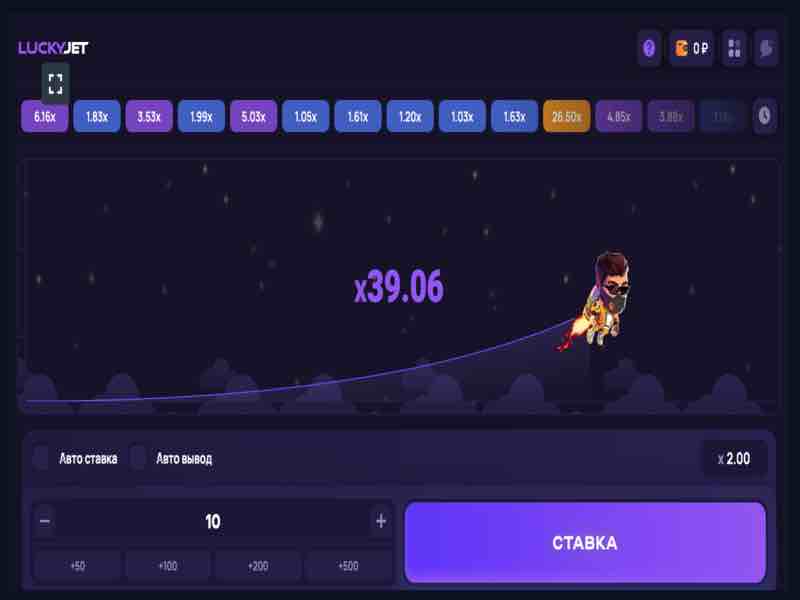
Lucky Jet is a rapidly growing online game. Lucky Jet has become a hit at 1win online casino. Every day more and more players discover Lucky Joe with his backpack in Lucky Jet. Why are more and more players choosing Lucky Jet?

Reasons for the popularity of the online game Lucky Jet
Lucky Jet — analogue of Aviator and Crash games

Yes, your favorite game is always your favorite, but have you ever had such a situation when the interface of an online game is a little boring and even a little annoying? If you play often, then this is possible. Lucky Jet is the same as Aviator or Crash, but a different interface. Instead of an airplane, you follow Lucky Joe with his backpack. And the rules of the game are the same — place a bet and withdraw money until the moment when Lucky Joe began to gain height.
The Lucky Jet’s maximum odds is 200
You control the game of Lucky Jet

Only you decide when to withdraw your money while playing Lucky Jet. Hold and take risks, or withdraw immediately, but with a guarantee of a small win? Very different strategies for different players, but the principle is the same — you decide when to stop and fix the win. Or a loss if luck was not on your side.
The Lucky Jet game is adrenaline and excitement in its purest form
How to play and win at Lucky Jet
The first step to winning at Lucky Jet is choosing a strategy and tactics for the game. Playing consciously is the choice of successful players. As an example, we can give two different and even opposite strategies.
Strategies and tactics in Lucky Jet

Cautious strategy of playing Lucky Jet
Risky strategy of playing Lucky Jet

Of course, Lucky Jet has strategy options in the middle — not so cautious, but also not so risky strategies of the game. For example, play with a multiplier x2-x3. The chances are about 40% — 45%, that is, even if the bet is lost in the next round, it is possible to win back and even make money.
In any case, playing Lucky Jet from 1win online casino requires care. First, define your goals and answer the question: «Why am I playing Lucky Jet?» There are two main answers.
The meaning of the game in Lucky Jet
- For pleasure;
- For money.

Depending on the answer to this question, decide how to play Lucky Jet. Play for money or for fun is your choice. Good luck with your new game. Great odds and may luck be on your side!

Eugene Vodolazkin / article author
I’m Eugene Vodolazkin, a passionate individual with a knack for gambling analysis, writing, and casino gaming. My expertise lies in the exhilarating Aviator crash game, which I have extensively studied and mastered over the years. As a gambling analyst, I provide valuable insights and advice to both players and casinos, leveraging my keen eye for trends and opportunities. With a flair for writing, I share my experiences and observations through engaging articles, shedding light on various aspects of the casino world. When I’m not analyzing or writing, you’ll find me immersing myself in the Aviator crash game, testing my skills and strategies in different casinos.
- Aviator
- Plane game
- Lucky Jet game
- JetX game
- Rocket X game
- Space XY game
- Cash or Crash game
- Reviews
- Strategies and tactics
- Download Aviator app
- Play Aviator 1win online
- Play Aviator 1xbet online
- Play Aviator Pin-Up online
- Play Aviator FairSpin online
- Play Aviator Slottica online
- Play Aviator AllRight online
- Play Aviator Vulkan Vegas online
- Play Aviator MostBet online
- Play Aviator Biamo online
- Play Aviator Parimatch online
- Play Aviator Red Dog online
- Play Aviator FastPay online
- Play Aviator 1xSlots online
- Play Aviator InstantPay online
- Play Aviator Fight Club online
- Play Aviator Betano online
- Play Aviator Codere online
- Play Aviator Wplay online
- Play Aviator Rushbet online
- Play Aviator 4rabet online
- Play Aviator Eurobet online
- Play Aviator Leovegas online
- Play Aviator Betplay online
- Responsible Gambling
- Privacy Policy
- About Us
- Terms and Conditions
- Information disclosure
RESPONSIBLE GAMING: At https://aviator-games.casino/, we place a strong emphasis on responsible gaming for both our partners and players. We believe that online casino gaming should be an enjoyable and positive experience, without any concerns about losing money. If you find yourself becoming upset or overwhelmed, we recommend taking a break to prioritize your well-being. To support you in maintaining control over your casino gaming experience, we provide a range of helpful resources and strategies.
PLAY RESPONSIBLY: Playing responsibly is a top priority at https://aviator-games.casino/, an independent website that is not affiliated with the websites we endorse. Prior to engaging in any form of gambling or betting, it is essential that you verify that you meet all applicable age and legal requirements. Our website is designed to provide informative and entertaining content, with the aim of enhancing your gaming experience. Please note that any links you click on our website will redirect you to their respective destinations.
All rights to the Aviator game belong to Spribe . Spribe OÜ is licensed and regulated in the UK by the Gambling Commission under account number 57302. Spribe specializes in innovative iGaming products and casino games.
This site uses cookies. Some of these cookies are essential, while others help us improve your experience on the Website. For more detailed information on the cookies we use, please check our Privacy Policy.
If you are a WordPress user with administrative privileges on this site, please enter your email address in the box below and click «Send». You will then receive an email that helps you regain access.
Выбираем любой слот из списка ниже и тратим там все полученные фриспины:
Онлайн-казино «1Win» © 1992—2021, все права защищены. Является зарегистрированной торговой маркой.
Особенности и преимущества приложения «1win»:
Регистрируйте новый аккаунт и получайте бонус на свой первый депозит. Выбирайте событие, вносите депозит и получайте бонус от 1Win
TapTap Global TapTap · Инструменты
Content Бонусы и Акции 1WIN (1ВИН) in Partners – обзор партнерской программы Как зарабатывать на партнерской программе 1win? Отзывы пользователей о 1WIN (1ВИН) вин канал Винлайн Особенности партнерки 1Win FAQ по партнерской программе 1 Win Статьи про арбитраж трафика Какие виды оплат есть в реферальной программе 1 Win? Партнерка 1win: партнерская программа БК Поддержка пользователей …
Смотрите с 1win Игровые Автоматы 1win Nnn Official 10 ищут:
- Скачать Бесплатно Слоты 1вин
- 1win Рулетка
- 1вин Автоматы 1win Ijb Xyz
- 1win Автоматы 1 Win17
- 1win Автоматы 1win Vbn Official Azurewebsites
- 1win Играть Зеркало Слоты Скачать